Show HN: Stickerbox, a kid-safe, AI-powered voice to sticker printer

More Stickers, On Us!More Stickers, On Us! Join the Stickerbox club and get a free 3-pack of paper rolls for your next creative spree. Plus, enjoy early access to new drops, tips, and ideas to keep the fun rolling.
TP-Link Tapo C200: Hardcoded Keys, Buffer Overflows and Privacy

Hi friends and welcome to the last post for this year! Whenever someone asks me how to get started with reverse engineering, I always give the same advice: buy the cheapest IP camera you can find. These devices are self-contained little ecosystems – they have firmware you can extract, network protocols you can sniff, and […]
Reverse Engineering Major US Airline’s PNR System and Accessing All Reservations
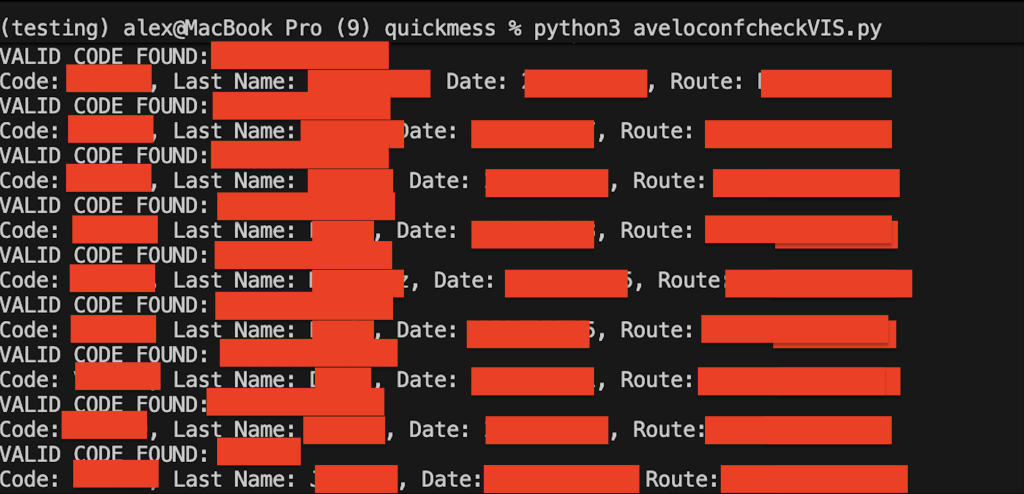
Timeline & Responsible Disclosure Initial Contact: Upon discovering this vulnerability on October 15, 2025, I immediately reached out to security contacts at Avelo Airlines via email. October 16, 2025: The Avelo cybersecurity team responded quickly and professionally. We had productive email exchanges where I detailed the vulnerability, including the lack of last name verification and […]
Performance Hints (2023)
Jeff Dean, Sanjay Ghemawat Original version: 2023/07/27, last updated: 2025/12/16 Expand all details Collapse all details Over the years, we (Jeff & Sanjay) have done a fair bit of diving into performance tuning of various pieces of code, and improving the performance of our software has been important from the very earliest days of Google, […]
Show HN: I Made Loom for Mobile
Streamers & Live Content Stream mobile web games, react to content, or share your browsing live. Face cam, touch indicators, direct to your audience. Mobile web gaming streams Live reactions to web content Tutorial streams Multi-platform streaming
I have to give Fortnite my passport to use Bluesky
Before we get started, just a reminder that Spitfire News is currently having its first-ever SALE to celebrate hitting 10,000 subscribers! Get $10 off an annual subscription for a limited time! Or subscribe for free to get unpaywalled editions like this one. I’m from Ohio, which means around this time every year I’m there for […]
TikTok Deal Is the Shittiest Possible Outcome, Making Everything Worse

from the mission-accomplished! dept There were rumblings about this for a while, but it looks like the Trump TikTok deal is done, and it’s somehow the worst of all possible outcomes, amazingly making all of the biggest criticisms about TikTok significantly worse. Quite an accomplishment. The Chinese government has signed off on the deal, which […]
Cursor Acquires Graphite

I’m thrilled to announce that Graphite has signed a definitive agreement to join Cursor. This deal brings together the best-in-class tools for creating, reviewing, and merging code in the age of AI. Graphite will continue to operate as an independent product, now with even greater resources to help our customers ship faster. Defining the new […]
Graphite Is Joining Cursor

The way developers write code looks different than it did a few years ago. But reviewing those changes, merging them safely, and collaborating on them has increasingly become the bottleneck for building production-grade software. The team at Graphite has spent the past few years thinking deeply about these workflows and have built a code review […]
Exploring Mathematics with Python
Exploring Mathematics with Python Arthur Engel Andrew Davison The heart of this book is Arthur Engel’s 1993 textbook Exploring Mathematics with your Computer which utilizes Turbo Pascal for its exploratory work, and is still available for purchase. The first six chapters (and Appendix A) are essentially that book, but with the programming language changed […]