Phoenix: A modern X server written from scratch in Zig
Phoenix is a new X server, written from scratch in Zig (not a fork of Xorg server). This X server is designed to be a modern alternative to the Xorg server. Current state Phoenix is not ready to be used yet. At the moment it can render simple applications that do GLX, EGL or Vulkan […]
Hacking a Java Minecraft server with memory overflows using in-game mechanics
Steam Store Is Offline

Steam Status · Is Steam Down? Refreshing in 45 seconds This website requires JavaScript There have been 166,000 page views on this site in the past hour, this indicates an issue with Steam. Steam Services Loading… In-Game on Steam Websocket Error Steam Store Offline Steam Community Steam Web API Service Unavailable Steam Connection Managers 95.2% […]
Keystone (YC S25) is hiring engineer #1 to automate coding

About Keystone We’re building AI-native error monitoring that automatically investigates production issues and generates code fixes. Think Sentry, but built from the ground up for a world where AI can actually understand your codebase, trace through logs, and tell you exactly what broke and how to fix it. We’re starting here and expanding until we’re […]
Show HN: Lamp Carousel – DIY kinetic sculpture powered by lamp heat
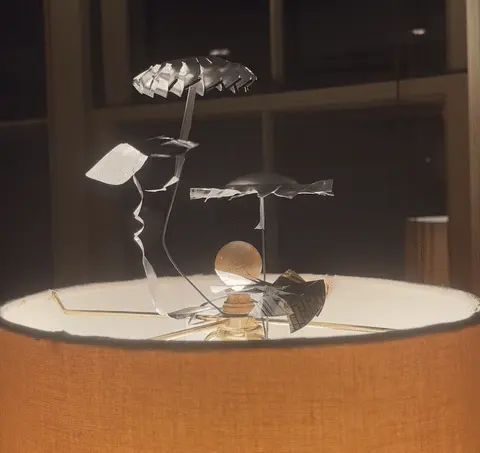
Can Spinners 2024-12-24 I came up with these little spinning doodads a few years ago around Christmas, and I haven’t seen anything like them online, so I’m writing about them here as they are quite fun to make. I’ve just been calling these things “can spinners” (ChatGPT suggested “twirluminum”). They remind me a bit of […]
Build Your Own 100TB NAS in 2025: Complete TrueNAS Storage Guide

Quick Answer# Building a 100TB NAS in 2025 is easier and cheaper than ever. Here’s what you need: Operating System: TrueNAS SCALE (Linux-based, Docker support, actively developed) Drives: Eight 18-22TB CMR enterprise drives (Seagate Exos X20, WD Ultrastar HC560, or Toshiba MG series) Motherboard: Supermicro X12STH-F with IPMI, 8 SATA ports, and ECC support CPU: […]
Spaced Repetition for Efficient Learning
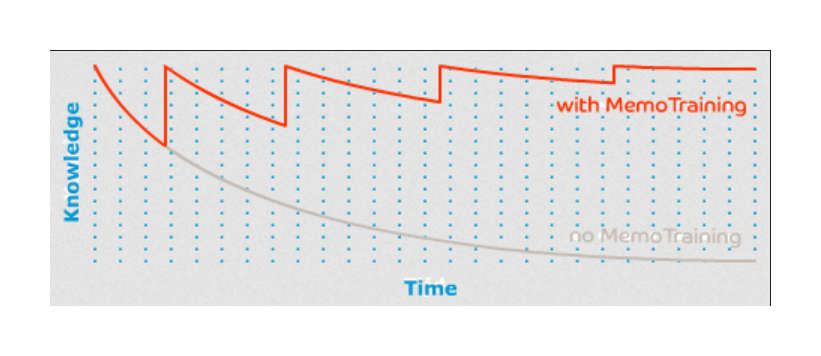
When should one review? In the morning? In the evening? Any old time? The studies demonstrating the spacing effect do not control or vary the time of day, so in one sense, the answer is: it doesn’t matter – if it did matter, there would be considerable variance in how effective the effect is based […]
Show HN: Minimalist editor that lives in browser, stores everything in the URL
What is this madness? A minimalist text editor that lives entirely in your browser and stores everything in the URL hash. Yes, you read that right. Your entire novel is now part of the address bar. Good luck sharing that link! Features (aka things that make this ridiculous) 📝 It’s a textarea! Actually not. 🗜️ […]
European Majority favours more tech regulation

To celebrate the launch of YouGov’s new European Political monthly survey, a new YouGov study of seven EU countries – France, Germany, Italy, the Netherlands, Poland, Romania and Spain – examines public attitudes social media regulation and banning political advertising from social platforms. Do Europeans think social media companies are regulated enough? The French are […]
Looking for Decent Conversation?
If you have fond memories of misspending entirely too much of your youth on web-based message boards, or you would like to misspend more of your nights and weekends on them now, Google has you covered. Simply add inurl:viewtopic.php to any query, and most, if not all, of your results will be discussion threads on […]